In this document, the result of the collaboration between the American NSA and the FBI, a new threat to the penguin is highlighted. Drovorub is a malware toolset, created by a Russian cyber espionage group, capable of infecting GNU/Linux systems.
Drovorub "woodcutter", the Swiss army knife of malware for GNU/Linux
According to the document released by the American agencies, Drovorub is a state malware, created by the Soviet military unit number 26165 of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main SpecialService Center (GtsSS). It allows for many advanced cracking operations, such as data theft or remote control of the victim's computer, and is extremely complex to find within the system.
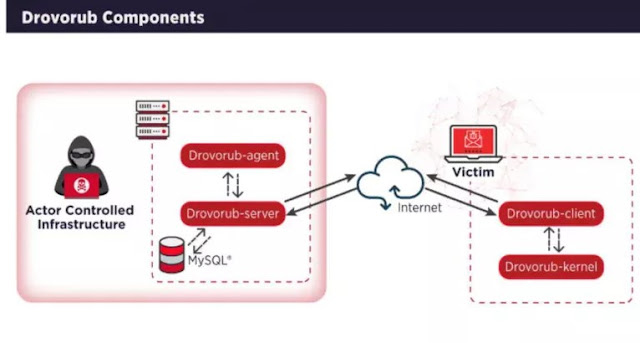
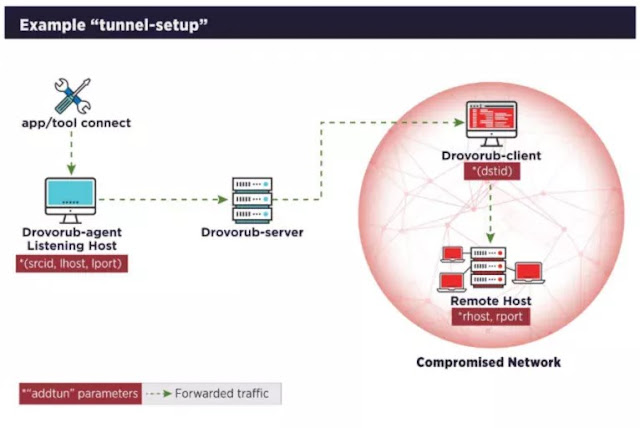
Drovorub can be considered as an aggregate of four components, each with specific and very advanced functionalities. These independent tools, among other things, are able to exchange data in the form of Json via WebsSocket. In particular, the macro components are:
- Drovorub-client, to create direct communication with the hacker-controlled infrastructure;
- Drovorub-kernel module, the actual rootkit;
- Drovorub-agent, a tool for file transfer and port forwarding of network traffic;
- Drovorub-server, to allow coordination and control of the whole.
The mitigations to be adopted
The NSA document explains, in detail, what are the actions to be taken to mitigate the threat. In particular, it is important to update the Linux kernel to version 3.7 or later. Starting with this release, in fact, a patch has been introduced to introduce digital signatures of kernel modules, thus preventing the execution of unsigned modules. Therefore, activation of the UEFI Secure Boot is also required. This operation, among other things, involves the exclusion of many incompatible distributions, especially in older versions.
In addition, this document has also been published by McAfee, which highlights other best practices to keep in mind, additional to those suggested by US government sources. The main rules to follow are:
- Perform a periodic scan to identify rootkits, backdoors, and other possible exploits. The suggested tools are Chrootkit and Rkhunter ;
- Enable SELinux;
- Control access to the API;
- Remove unused software, disable unnecessary services;
- Make a backup of your system.










0 Comments